Protect yourself and your server from known vulnerabilities such as DROWN, POODLE, CRIME, BREACH, FREAK, Logjam, Heartbleed, and BERserk.
SSLv2 and SSLv3 are both obsolete protocols that have many vulnerabilities. Most recently the DROWN and POODLE attacks, but also CRIME, BREACH, FREAK, Logjam, Heartbleed, and BERserk. SSLv2 was deprecated in 2011 and SSLv3 was deprecated in June 2015. So, for your own safety and the safety of your users, both protocols should be disabled on all your servers various services. Note that this is a requirement for PCI Compliance as well.
The DROWN attack allows cross-protocol attacks, so disabling vulnerable protocols across of your services that use the same SSL Private Key is required in order to be safe.
Below is an alphabetical list of commonly used applications throughout the Vivio Hosting experience, and will show you how to make the necessary changes if they are needed.
How to disable SSLv2 & SSLv3 in Apache:
You'll need to login to the command line as root over SSH. From there, on CentOS-based systems, you'll need to edit /etc/httpd/conf/httpd.conf. On Debian/Ubuntu-based systems, you'll need to edit /etc/apache2/mods-enabled/ssl.conf.
After opening that file, you'll need to set "SSLProtocol" to the following:
SSLProtocol ALL -SSLv2 -SSLv3
Then restart Apache, on CentOS, run: /etc/init.d/httpd reload On Debian/Ubuntu, run: /etc/init.d/apache2 reload
How to disable SSLv2 & SSLv3 in Dovecot:
You'll need to login to the command line as root over SSH.
For Dovecot 2.1+, edit /etc/dovecot/local.conf to add the below lines and then restart Dovecot.
ssl_protocols = !SSLv2 !SSLv3
For Dovecot 2, edit /etc/dovecot/conf.d/10-ssl.conf to add the below lines and then restart Dovecot.
ssl_cipher_list = ALL:!LOW:!SSLv2:!SSLv3:!EXP:!aNULL
How to disable SSLv2 & SSLv3 in Exim:
You'll need to login to the command line as root over SSH.
Edit Exim configuraiton file /etc/exim.conf and change tls_require_ciphers to:
tls_require_ciphers = ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM:!SSLv2:!SSLv3
Restart Exim.
How to disable SSLv2 & SSLv3 in Pure-FTP and Pro-FTP:
You'll need to login to the command line as root over SSH.
For Pure-FTP, edit /etc/pure-ftpd.conf
For Pro-FTP, edit /etc/proftpd/proftpd.conf
Change the TLS Cipher Suite to:
HIGH:!aNULL:!eNULL:!PSK:!RC4:!MD5:!TLSv1:!SSLv2:!SSLv3
How to disable SSLv2 & SSLv3 in Lucee:
By default uses HTTP/1.1, so unless it has been specifically changed in the server.xml you are safe.
How to disable SSLv2 & SSLv3 in Nginx:
You'll need to login to the command line as root over SSH.
Modify the ssl_protocols directive to only use TLSv1, TLSv1.1, and TLSv1.2. If you do not have a ssl_protocols directive, add it to the top of your configuration file.
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
How to disable SSLv2 & SSLv3 in Postfix:
You'll need to login to the command line as root over SSH.
Edit /etc/postfix/main.cf, and confirm the following settings:
- smtpd_tls_protocols = !SSLv2, !SSLv3
- smtp_tls_protocols = !SSLv2, !SSLv3
- lmtp_tls_protocols = !SSLv2, !SSLv3
- tlsproxy_tls_protocols = $smtpd_tls_protocols
- smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3
- smtp_tls_mandatory_protocols = !SSLv2, !SSLv3
- lmtp_tls_mandatory_protocols = !SSLv2, !SSLv3
- tlsproxy_tls_mandatory_protocols = $smtpd_tls_mandatory_protocols
- smtpd_tls_ciphers = medium
- smtp_tls_ciphers = medium
- smtpd_tls_dh1024_param_file=${config_directory}/dh2048.pem
- smtpd_tls_eecdh_grade = strong
- smtp_tls_exclude_ciphers = EXPORT, LOW, MD5, aDSS, kECDHe, kECDHr, kDHd, kDHr, SEED, IDEA, RC2
- smtpd_tls_exclude_ciphers = EXPORT, LOW, MD5, SEED, IDEA, RC2
How to disable SSLv2 & SSLv3 in Railo:
By default uses HTTP/1.1, so unless it has been specifically changed in the server.xml you are safe.
How to disable SSLv2 & SSLv3 in Webmin & VirtualMin:
After logging into Virtualmin, click Webmin -> Webmin -> Webmin Configuration -> SSL Encryption. Where it says "Allowed SSL ciphers", set the option "Only strong PCI-compliant ciphers", and click "Save".
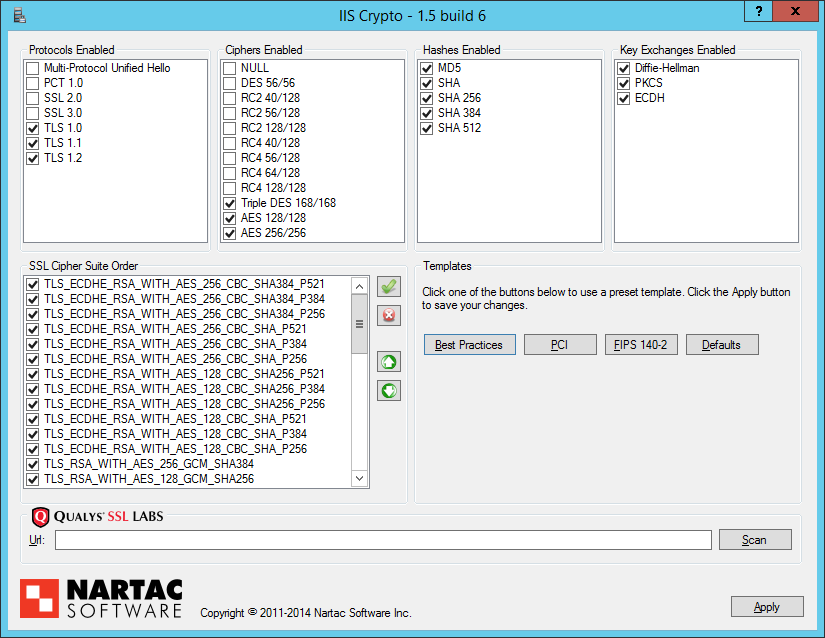
How to disable SSLv2 & SSLv3 in IIS:
You'll need to login via RDP as administrator.
Then download IISCrypto for your specific version of windows from Nartac Software:
https://www.nartac.com/Products/IISCrypto/Download
.Net 4.0 for 2012 and higher
.Net 2.0 for 2008 and lower
Run the tool, and deselect SSL 2.0 and SSL 3.0 in the Protocols Enabled section.
- This will also be deselected if you use any of the 3 Templates (Best Practices, PCI, or FIPS 140-2).
Click Apply
Reboot the server to apply the changes.